Working with Symplified
Posted 31 August 2012, 19:00 | by Ben Duguid | Perma-link
I've been working on a couple of Proof of Concept demos for a client that's looking to implement a Single Sign On solution on their new site, and one of the offerings was from Symplified. Seeing as there doesn't appear to be much out there on this, especially within an ASP.Net context I thought I'd write up my experience.
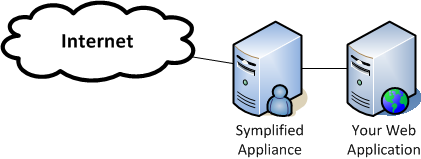
The first thing to realise is that Symplified works as a reverse proxy, sitting between your server and your users (reverse in that it's a proxy you put in place rather than your user's ISP). So all requests hit the Symplified app server first before they are forwarded on to your servers. All authorisation is handled by the Symplified app, so you shouldn't be locking things down with the authorization elements in web.config files.
However, you can still use some of the features that the framework provides you with a bit of care.
Membership Provder
I started off with the idea of implementing a custom Membership Provider to handle the authentication/authorisation aspects (as this had worked well in the previous PoC based on PingFederate).
CreateUser
You can still implement the CreateUser method in a custom membership provider, as you will need to provision users within Symplified, especially if you want to allow direct registration.
In Symplified's world, you will need to make three calls to a rest service:
- Create a session token
- Create a user
- Reset the user's password
You need to reset the password as by default the users appear to be created with an expired password, and resetting it to the same value fixes this - note that Symplified will also send an email to the user informing them that they've reset the password - you may want to suppress this.
Not too bad, however handling errors from the create user service is a little tedious:
- If any of the parameters don't match the patterns expected you'll get a 500 lnternal Server error returned with plain text error messages in the XML response.
- If the user already exists you'll get a 400 Bad Request, again with the error description in the XML.
These plain text error messages will need to be parsed and mapped to MembershipCreateStatus values to get sensible errors back to your controls.
ValidateUser
You can't really implement the ValidateUser method however, as there's nothing in the API you can call to do this, the user's login credentials need to be sent directly to Symplified's SSO application so it can set it's cookies appropriately, and then pass some headers through to your "secure" areas.
So, how do you handle an authenticated user?
When the user is viewing a "secure" area of your site, Symplified will send a number of additional headers along with the request, which will include things like the Username, which can then be used to generate a Forms Authentication ticket and a Membership Priniple that you can fill for the app to use later.
For the PoC I implemented that logic in a custom Module that hooks into the application's AuthenticateRequest event.
OpenId Users
The one big issue so far has been around users authenticating via OpenId providers. These users are authenticated without a user being be provisioned in Symplified, which could well be an issue for you. The solution we put in place within the PoC was to check for the headers stating this was a login from the OpenId provider, and then attempt to create a user within Symplified, and ignoring the duplicate username error message - the Symplified engineers were looking at adapting the solution so that if the OpenId user matched known user it would send additional headers which would allow me to skip the creation step.
Next Steps
If we decide to go forward with Symplified there are a number of changes I'd like to make:
- Only create the user context if the request comes from the Symplified app.
- Implement the GetUser methods using the Symplified API.
- Redirect requests to the Symplified applicance if they don't come from there.
- Don't try and create the user on every single request!
Filed under: ASP.NET, SSO